In terms of growth, the premise is simple online: Big things are slower, small things are quicker. That’s why the most efficient way to scale businesses faster is to outsource some of their processes.
And you might think outsourcing is a recent phenomenon because the digital revolution made it possible for people to share their skills and talents to organizations even halfway across the world.
But people have been outsourcing all their lives. We outsource cooking to restaurants. We outsource cleaning our homes to cleaning services. We outsource producing electricity to electrical companies.
There are things that we can do ourselves but outsourcing makes it more convenient for us. And there are things that we can’t really do, whether we don’t have the expertise or we don’t have time, that should be outsourced.
It’s been an established transaction and it’s very beneficial, especially for startups to outsource talent at first to have a good foundation before scaling.
Outsourcing is Beneficial And Crucial at Times
For example, let’s say that I am a local business that creates custom furniture. I have been in business for 5 years and the growth has plateaued. I figured that in order for my business to experience growth again, I need to show my products to a wider audience to also grow my customer base.
And the fastest way to do that is to go online. Although ultimately, I’m not a startup because I already have an established business, I’m still an online startup. I don’t have the online infrastructure setup to have a working online store and a marketing process to grow my audience.
So because I have a diverse need of talent to set up my online store, I decided to employ an agency so that they could provide the manpower I need.
Well you can say that in order to save money when starting out, I can just learn how to do it myself and make my own online store. Platforms like Shopify makes it easy, even for people with no technical background, to start on Ecommerce.
However, as a business owner, I still need to make sure that my “bricks and mortar” business is still operational and our current customers are not left out while I migrate online.
So outsourcing is the only good solution to do that.
Most of the processes that businesses outsource are the ones that require expertise and the ones that can be performed while away from the business’s location.
Expertise and experience takes time. Having people that already have experience and expertise will remove a huge bulk of time from business founders and its core team.
And outsourced experts can also impart their knowledge to the organization. They know the day-to-day processes so they will only teach all the necessary skills and remove all the fluff that some certifications or courses have.
The most common business processes that are outsourced are customer service and marketing. However, there are other business processes that you can also outsource:
- Admin Tasks
- Accounting
- Cyber Security
- Human Resources
- IT Management
- Logistics/Shipping
- Manufacturing
- Research and Development
- Sales
And so much more services. Basically, any process that you have in your business, you can outsource. But we are going to focus on outsourced data analytics because it arguably gives the most access to outsourced partners.
The Risk With Outsourced Partners
We have established earlier that outsourcing provides much needed speed to clients. And with speed comes risks. That is the reason why we have speed limits. The faster you go, every mistake gets amplified, so it’s up to you to balance risk vs reward.
And with outsourcing, we have inherent risks as well. When you want your house cleaned by professionals, you typically let strangers know where you live, let them enter your house, and even let them access sensitive parts of your home.
I didn’t mean to make you paranoid but that’s really what happens every time we employ someone to work on our home.
And that’s quite the same with outsourcing, especially with data. We let strangers access our files and even customer data in order for them to do their job. To be more specific, here are the typical data that clients share to outsourced partners:
- Email Addresses
- Login Credentials
- Social Media Accounts
- Files
- Advertising Accounts
- Customer Data
Anyone who has access to these files has a huge responsibility to keep it safe. And having bad actors access any one of these files is going to be devastating for the business and the owners of the data, the customers.
There are multiple bad things that can happen to those if fallen in the wrong hands:
- The organization can be extorted for money in exchange for the data
- The data can be sold on the black market or on the dark web
- Files can be maliciously deleted
- Social media accounts can be changed and used for the hackers gain (usually to promote crypto)
- Advertising accounts can be sabotaged or have the data sent to competitors
- Customer data can be used to hack their accounts or even sell them to the black market or deep web
So it’s very risky to outsource data analytics when we have these risks involved.
How To Combat Risks From Data Analytics Outsourcing
I think we have emphasized enough that speed amplifies risk, so we might think that slowing down the process already eliminates the risk. But it doesn’t.
To completely be safe in sharing your files for outsourced data analytics, a robust security protocol must be implemented.
First step to making sure that your data and your customers’ data is safe when employing outsourced data analysts is vetting.
Vet Agencies and Freelancers Before Working With Them
This might seem too obvious but some organizations skip this step. Yes, it’s important to be open and have a trusting mindset when it comes to working with people.
However, a little bit of scrutiny on an organization is more than warranted, it’s even appreciated by freelancers and agencies alike. Because if an organization did their due diligence before contacting an outsourced partner, those partners will have an impression that it’s going to be a productive relationship.
They know that most of the work will still be done by the partners, but they also know that the organization is also willing to do their part.
After all, the biggest risk when outsourcing data analytics is working with the wrong partner.
Check out their reviews on freelancing platforms, interview clients that the agency has already worked with, and gather as much information as you can.
If possible, talk to at least one organization that gave high ratings and one organization that gave low ratings. If not, talk to one organization that gave the partner neutral ratings.
Emotions often amplify ratings making ratings somewhat subjective. Interviewing clients that gave a high and low rating often gives you the full picture of a partner’s pros and cons.
And interviewing a client with a neutral rating will be detached from having emotions, thus giving a fairer, more objective evaluation of a partner’s working experience.
However, this is not always the case. Even the best rating systems or testimonials always have a hint of bias within them. So take everything with a grain of salt.
As much as you can, take time on gathering any information you can get. Weigh in your options. And talk to previous clients.
As a side note, talking to other clients that the agency or freelancer worked with is a great exercise in itself. It’s creating connections with other business owners. Once you have been in contact, you can then ask them for other recommendations in the future. Sometimes, they will proactively recommend services to you if you already have good rapport with them.
All in all, talking to other businesses is a good thing.
Another thing to consider when vetting for the “right” data analytics partner is that most of the time, data leaks and other emergency security scenarios aren’t deliberately caused by bad actors.
Sometimes security breaches and other concerns are accidentally found or committed by non-hostile partners.
So the rest of the protocols that we have are for preventing accidental security mistakes, making data secure to avoid even harboring attention or temptation, and deterring bad actors from exploiting weaknesses in the system.
Though cyber attackers and bad actors exist, always remember Hanlon’s razor. Don’t assume that the leaks are malicious immediately, when they can be attributed to honest mistakes.
Having a “Trust But Verify” Mindset
Trust is a very important currency when it comes to online transactions. And it flows to all other services that you interact with.
For example, as a consumer, you trust that your banks are securing your money and have it ready for you when you need it. You trust that online transactions will go well and that your money goes to the intended recipient, and you will get the product or service that you paid for.
It’s a crucial aspect to everything online. And I believe that Ecommerce only boomed during the pandemic because people were forced to trust the platforms. They have no choice but to transact online because of the lockdowns.
However, because we were thrust to transact online, consumers saw that we can really trust the system and do our transactions online. Once that foundation was built, people became more comfortable and now online transactions are as normal and as mundane as ever.
The “Trust But Verify” (TBV) mindset is a proactive approach to security. It’s different from the default reactive mindset of security systems.
For example, going to a public establishment practices a bit of the Trust But Verify mindset. They will let you in only after having a quick inspection on you and your belongings.
However, the most effective example of a TBV approach are exclusive events. Aside from also performing the usual inspections, security also checks if you are on the guest list or if you have a pass. Even if someone passes the inspection but isn’t on the guest list or doesn’t have a pass, they won’t be let in.
The security is checking for your intent and necessity to be in that place. They are answering “Why are you here?” and “Is it essential for you or the event to have your presence?”
A practical application for the TBV approach is oftentimes missed by organizations. Usually, upper management or C-Suite Execs have a carte blanche access to all of the files and folders of the organization, even if it’s not necessary.
It’s even thought of as a “perk” of being a higher up. However, this is actually a liability. Because of the wider access given to higher-ups, they have been the most likely targets of cyber attacks. And this fact is corroborated by multiple articles.
There isn’t any actual reason for giving a disproportionate amount of access to higher-ups when they don’t need to process the data. And it gives a big risk when they are the most vulnerable to attacks.
So it should be protocol that access to directories, files, credentials, and so on, should be on a complete “needs” basis.
Outsourced partners should only be able to access sensitive data when they need it. And as soon as their needs have been fulfilled, access will revert back to a default “deny” state.
Think of it this way, doors have 2 functions. Covering what’s inside the room and having an interface for the people who wish to enter the room. The default state of doors are closed. So access to what’s inside the door is not accessible by default.
Have Proper “Security Hygiene”
Data security maintenance is kinda a weird term. Because maintenance has a root word of “maintain”. But in order to maintain data security, changes have to be frequently made.
Security “hygiene” is the most appropriate term for these best practices as it makes your data clean and safe, and it should be a regular habit.
Like, we all know that washing hands is important. But how do we know if we washed our hands properly? Some say that you should wash your hands to the tune of “Happy Birthday”. It might sound silly but Happy Birthday has the perfect duration for you to wash your hands to
A good example of security hygiene best practice is changing your passwords regularly. Mcafee recommends changing your passwords every 3 months.
This might sound like a large hassle but it’s the price to pay for security. I personally know the feeling when your brain runs out of ideas to make your password different enough but still easy to remember.
Here’s a scenario. Let’s say that you have already been working with an outsourced data analytics agency for 3 months. Then one employee accidentally attached a file with their login credentials in an email sent addressed to multiple people in the data analytics agency.
The employee immediately replied and asked for the recipients to ignore the attachment and if it was downloaded, to delete it immediately.
This scenario perfectly encapsulates what I meant earlier with the statement “preventing harboring attention or temptation.”
Some people on the agency received the email and just ignored it. And let’s say there was someone who was morbidly curious enough to open the attachment, and was even inclined to try it out. The individual on the agency really doesn’t have any malicious intent, though their actions are really improper.
So some people, even though they are really trustworthy and disciplined, might still be tempted to do improper acts when given the opportunity.
But because of the 3 month password refresh protocol in your organization, the curious employees at the agency failed to login.
So, the crisis was averted.
This is of course a fictional scenario where all the events lined up to perfection. But you can see how it can prevent data leaks and other cyber security concerns.
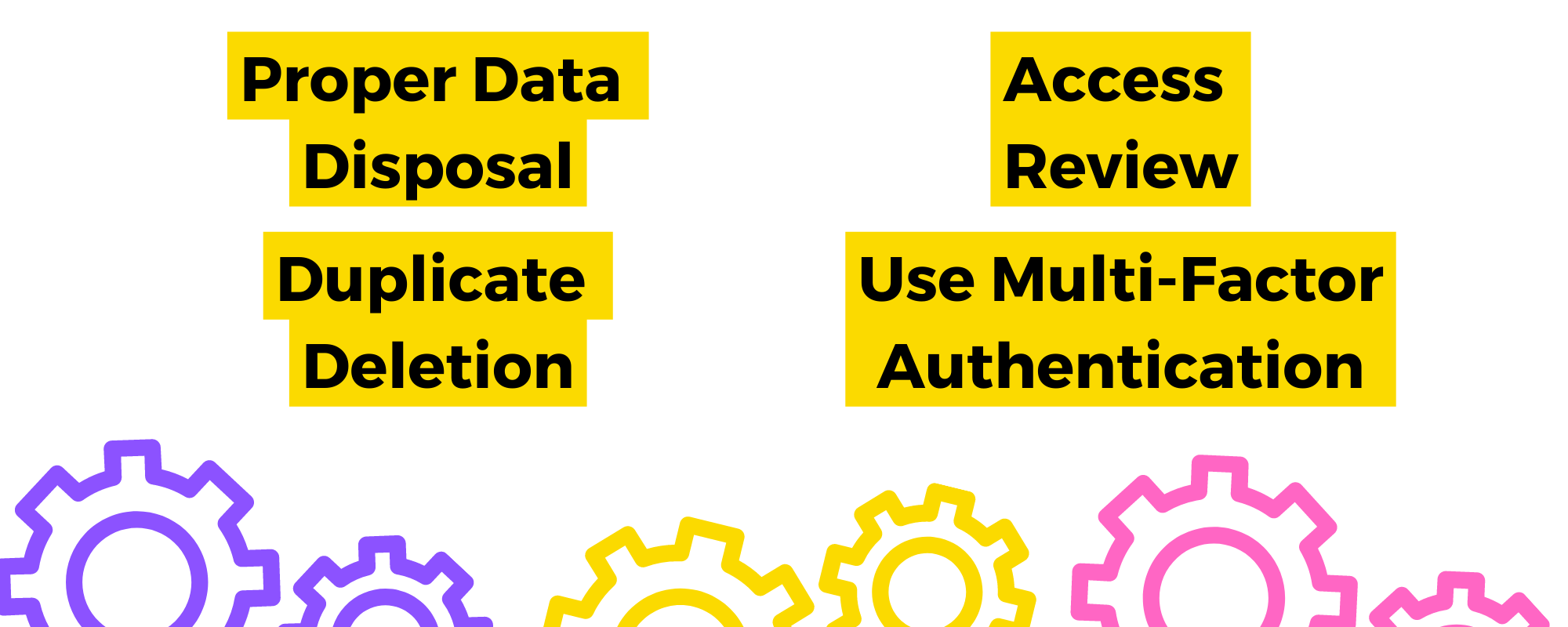
Here are some best practices you can follow:
- Proper data Disposal – One simple example with this is the deletion of files on your desktop. The common setup is if you delete your file, you can recover it from a form of a Recycle Bin.Though convenient if you accidentally delete files, it should not be accessed by partners. Put measures into place to prevent unnecessary access of Bin or Recycle Bin type functions on your system.
- Duplicate Deletion – Data duplicates are not really harmful. Sometimes they can just bog down the system because it occupies storage space. However, duplicates can be dangerous if they hold sensitive data.As much as possible, delete duplicates of files and directories. At the least, it can lessen the stress in your system and at best, it can prevent data leaks.
- Access Review – It pays to be sure. Even with protocols in place, access might be granted automatically by the system or by human error. It’s best to check and provide access to those who need and remove access to those who don’t.
- Use Multi-Factor Authentication – One way to prevent unnecessary access is to have multi-factor authentication. Your data analytics partner may have the login credentials to your accounts but they can’t really access it, unless you provide the authentication code.
Have Risk Management Protocols
Most of the security measures we have are being done in preparation of data being compromised.
However, risk management protocols should cover what people should do before a breach, during a breach, and after a breach.
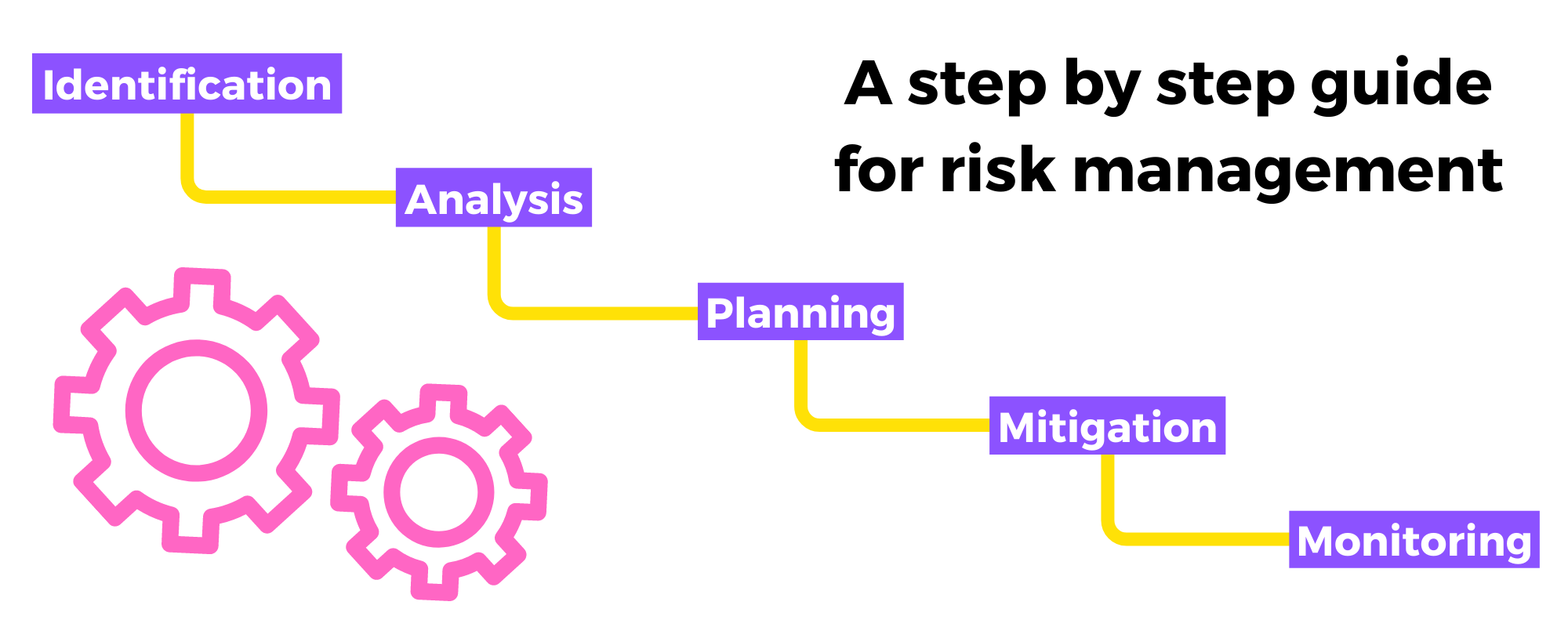
Here’s a step-by-step guide:
1. Identification – determine if a security risk happens.
- Did a file get accessed that should not be?
- Did a partner login unnecessarily? Is it accidental or intentional?
- Did customer data get leaked?
2. Analysis – determine the scope and scale of the security risk
- How many files were accessed?
- How many customer accounts got accessed?
- How many users were affected?
- Which departments are affected by the risk?
3. Planning – creating the steps to follow and the people involved
4. Mitigation – implementing what’s created in the plan
5. Monitoring – doing the process again and checking regularly
Lessening The Touch Points
The less people who have access to sensitive data, the easier it is to determine and prevent the risks. Here in our agency, USource, we have a Compliance Team that is composed of 3 members to handle all of the credentials of more than 100 employees.
It might seem a daunting task and it might seem like a huge bottleneck, but we have systems in place to make sure that the login process is still quick enough for the team members, but secure enough for the clients.
Additional credentials that clients will provide is also sent through a secure portal, only to be accessed by the Compliance Team.
Client credentials then are stored in a software and automatically entered into the login fields. Team members have no access to edit or view the credentials. And if updates are needed, the Compliance Team will update it for the team members or for the clients.
Having less touch points also minimizes complexity, makes it easier to track, and ensures that client data is secure.
Risk Cannot Be Eliminated, Only Minimized
Every little thing that we do has a risk tied to it. It might be insignificant at times but a risk is a risk. You can risk food poisoning on the food that you buy. You can have accidents whether you are driving or commuting to your work. You can receive fake products or not receive what you paid for if you do online transactions.
We know all these risks yet we still face them because we know that it’s worth it in the long run. So don’t be discouraged and swear off outsourcing your data analysis to agencies or freelancers.
Rather understand the possible risks, have measures in place, and face the risk. It can be helpful at the least or it might be the rocket fuel to boost your organization’s growth.